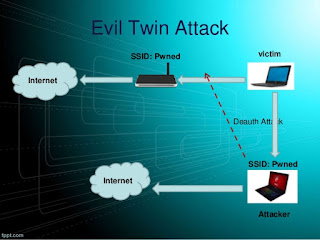
How to increase alexa rank tips
hello learner today i am gonna tell you how to increase alexa rank and what it is. Alexa is a very important and powerful tool to improve and rank your website/blog traffic. Alexa ranks sites based primarily on tracking a sample set of internet traffic. Alexa rank checker tool shows the current Global ranking, Reach, 3 month change of multiple domains within the Alexa rank system. This system is one that measures the traffic to a site by users so it's very important to many domain owners, buyers.
2.Install Alexa toolbar into your browser – The more Alexa toolbar users visit your blog, the better your ranking will be. You can’t decline this fact that you visit your blog more than any of your reader. So, why don’t you take advantage of your own visit
3.Add Alexa widget to your blog – Alexa widget helps Alexa servers to better track the traffic. Add one in your blog and see a significant improvement in your rankings. It may not work overnight but something is better than nothing, right?
4.Write Linkable and shareable content – The more useful content you’ll write for your blog readers, then more traffic and backlinks you’ll get. People will more likely to share your content across their social networks and finally it will help you in improving your Alexa rank fast.
5.Drive traffic from Social Media sites – If you are connected with other bloggers on social media, chances will be higher that they all are using Alexa toolbar. The more traffic you’ll get from your blogger friends the better chances will be to get a noticeable ranking.
6.Keep updating your blog with useful content and increase your returning visitors count – Trust me, returning visitors (Happy readers) help a lot to boost blog’s ranking. They are happy readers so they will share your content several times on their various social network profiles. You know how it will be beneficial for you. You know, right? Do let me know in the comments.
6.Showcase your Alexa rank to your social media friends/ bloggers friends and link back to your blog. It attracts huge clicks and your ranking will keep improving day by day. See, how I did that on facebook and got 100+ likes and 400+ traffic.